Navigating Your Future In Cybersecurity

We will spare you and skip the clichéd intro about cybersecurity’s significance in our digital age. The field of cybersecurity is booming, with a pressing need for experts to step into various specialized roles, each demanding a unique skill set.
When you hear ‘cybersecurity’, you might instantly think of penetration testers, but there’s a broader spectrum out there. It’s not just about the offensive; there are strategic planning roles, defensive positions, and beyond.
Let’s delve into some prominent career paths in cybersecurity to guide your career choice.

Enrolling in an initial cybersecurity course provides you with both a structured setting to acquire basic In cybersecurity, the inevitability of an incident is accepted; the focus is on when, not if, it will strike.
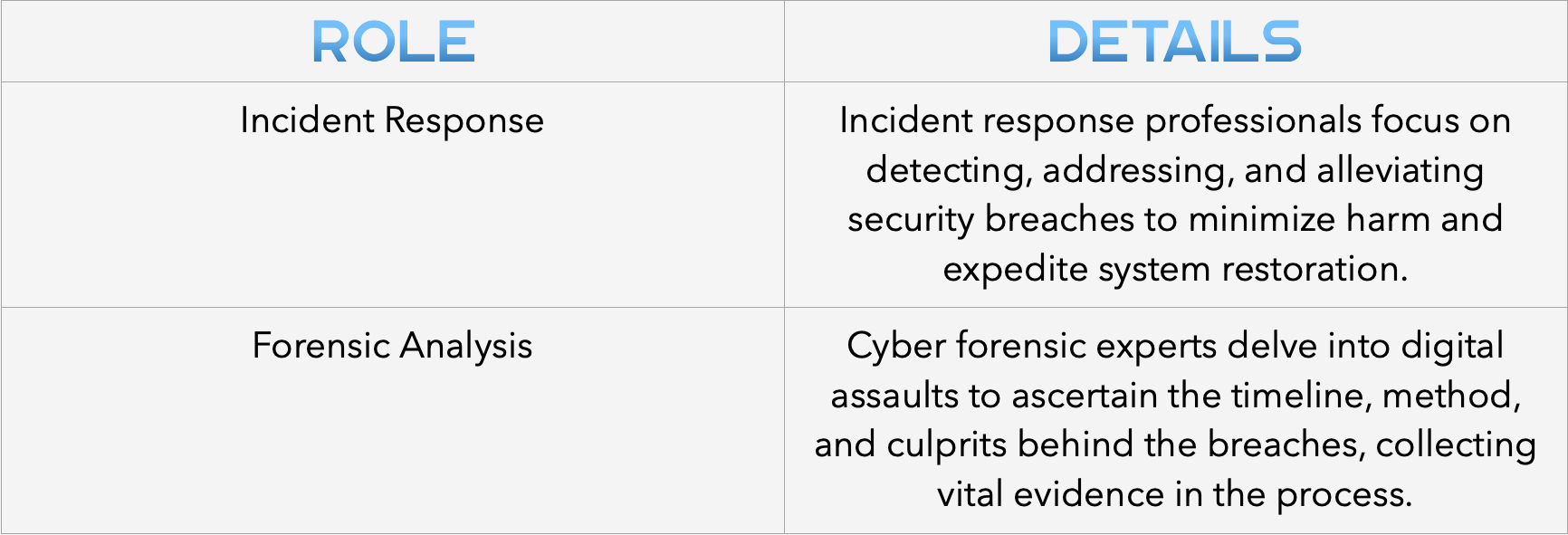
Incident response roles are centered around readiness for cyber threats and immediate action upon their occurrence.
Professionals in this niche craft comprehensive security strategies, defining procedures and roles for crisis management.
They might also dive into forensic analysis to trace an incident’s origins and specifics. Should the situation escalate, they collaborate with legal authorities to secure evidence that stands up in legal proceedings.
Choose this career if:
• Thriving in high-stress environments is your forte.
• Strategic planning and organization are your strengths.
• Tackling problems head-on excites you.
• Collaboration with others is where you shine.
• You have a penchant for detective work, much like Sherlock Holmes.
Skills you should hone:
• Expertise with tools for incident response and digital forensics, including EDR, IPS, IDS, and SOAR technologies.
• Interpersonal abilities such as effective communication, teamwork, and resilience under stress.
• A grounding in basic computing and network systems.
• A thorough knowledge of cybersecurity principles, structures, and practices.

Launching into a career in incident response requires a robust understanding of technology along with continual learning about new cyber threats.
Those already in tech or IT should focus on mastering cybersecurity fundamentals and gaining expertise in industry-specific tools and approaches, such as the NIST Incident Response Framework.
For individuals without a tech background, gaining practical experience alongside basic education is key. Starting with an entry-level IT position, like tech support or an IT tech role, could fast-track your transition into incident response.
Although some positions might favor candidates with degrees in fields like computer engineering or cybersecurity, formal education isn’t always necessary.

CompTIA Security+
GIAC Certified Incident Handler (GCIH)
GIAC Certified Computer Forensics Examiner (CCFE)
HTB Certified Defensive Security Analyst certification
SOC Analyst job-role path

Numerous educational programs in cybersecurity come equipped with virtual laboratories, offering a space where you can hone your abilities with authentic security tools in a controlled setting. These labs are seamlessly integrated into coursework, but the opportunity for practice doesn’t end there; you can establish your personal virtual lab as well. A fundamental lab setup generally consists of:
- A cloud platform for hosting virtual machines
- A target machine that serves as the subject of simulated attacks
- An attack platform, which is the machine from where you will devise and execute your strategies

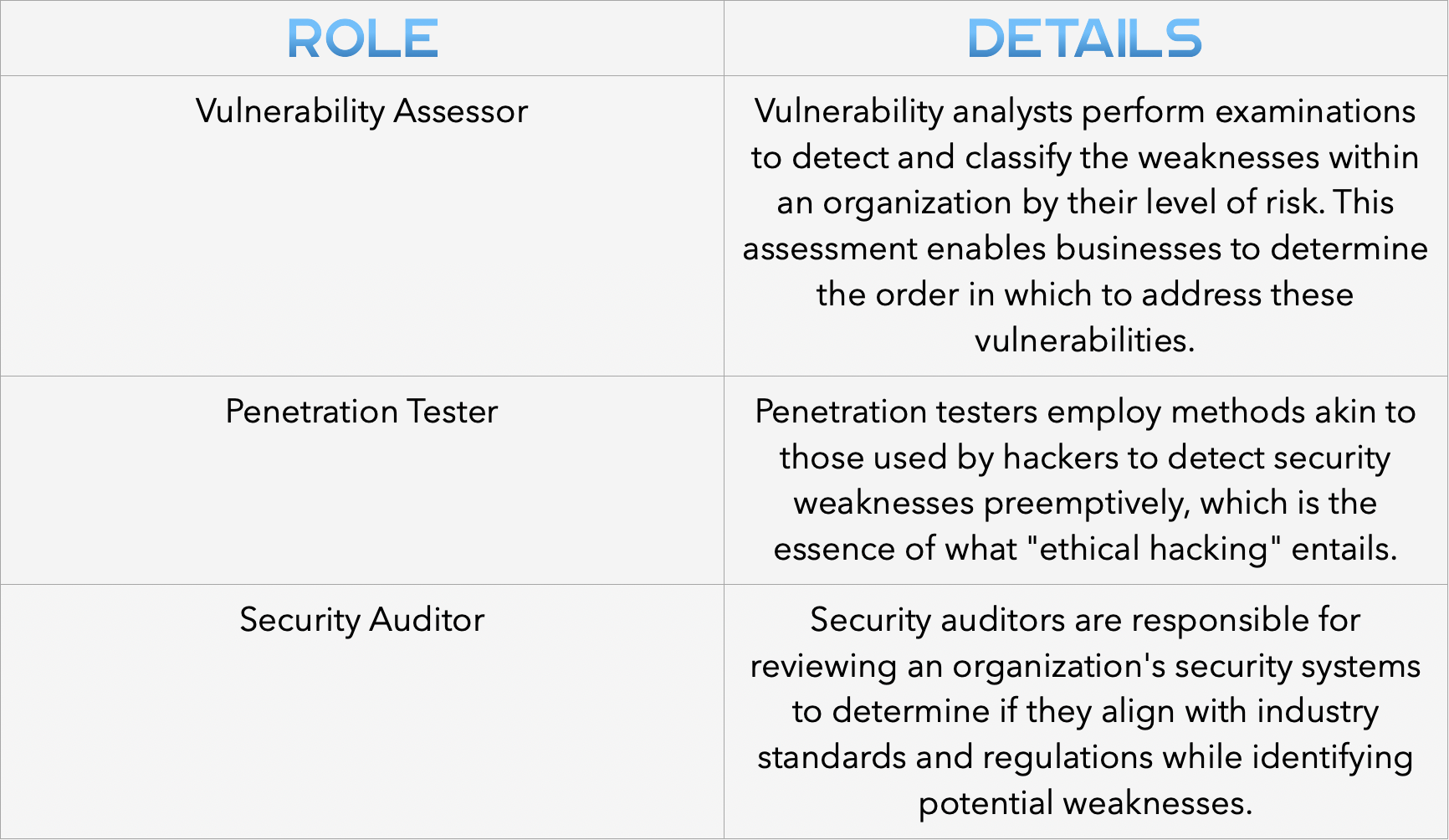
In the realm of cybersecurity, when we discuss testing, we’re looking at roles that assess the resilience of digital systems, networks, and assets. These professionals aim to uncover security flaws and vulnerabilities before they can be exploited maliciously.
Their role includes spotting weaknesses and threats that could compromise organizational assets. This encompasses evaluating everything from network defenses and access controls to the robustness of applications.
This avenue aligns with what’s often termed as “ethical hacking” or being part of a “red team,” where experts mimic actual cyberattacks to expose potential security breaches from an attacker’s viewpoint.
This career suits you if:
• You’re drawn to the role of an ethical hacker.
• Staying updated with current technologies and trends is something you enjoy.
• You possess a fervent desire for continuous learning.
• Discovering what others overlook excites you.
Skills to cultivate:
• Creative and analytical problem-solving skills.
• Expertise in penetration testing strategies, tools, and tactics.
• In-depth understanding of operating systems and network architectures.
• Basics of scripting and software development.
• Keeping abreast of emerging security flaws, methods, and trends.

CompTIA PenTest+ Certification: A well-regarded qualification in the industry that provides hands-on training ideal for those starting in penetration testing.
The Penetration Tester Pathway by HTB: Offers a guided progression into the profession, suitable for those with or without a background in the area.
Certification as a Hack The Box Penetration Testing Specialist (CPTS): This credential combines both theory and hands-on practice to prepare you for conducting actual penetration tests.
EC-Council Certified Ethical Hacker (CEH): A popular certification that teaches you to think and act like a hacker, but with ethical intentions, giving you the skills to identify vulnerabilities from an attacker’s perspective.

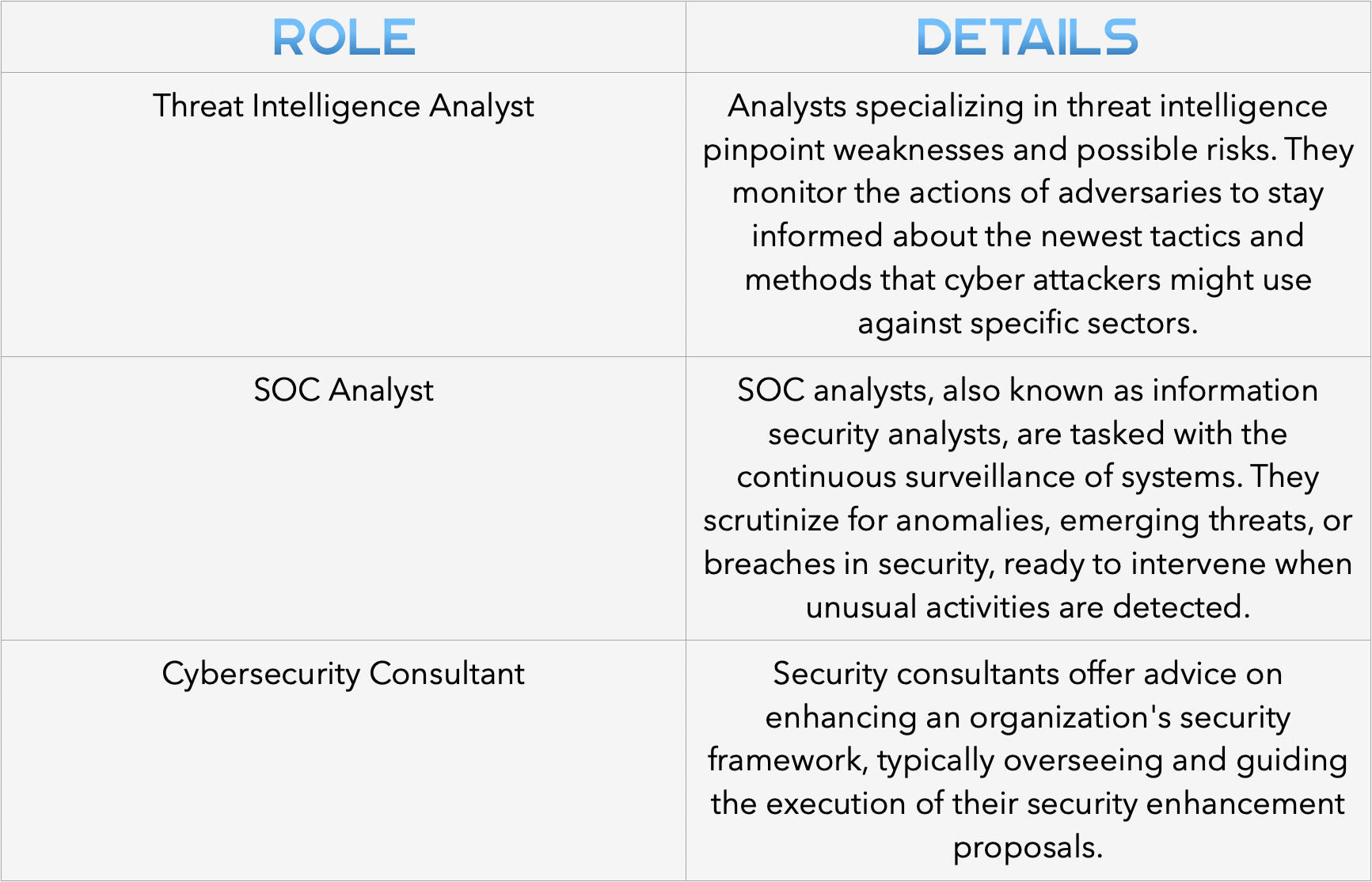
Within a Security Operations Center (SOC), a cybersecurity analyst focuses on safeguarding an organization’s digital infrastructure. Their role involves detecting threats, safeguarding assets from cyber intrusions, data breaches, and ensuring business continuity.
This profession offers various trajectories for advancement, serving as an excellent entry point for newcomers to cybersecurity, even those without previous experience.
Choose this path if:
• You believe in scrutinizing the minutiae to uncover issues.
• You possess a keen analytical mind with a logical approach.
• Connecting the dots comes naturally to you.
• Problem-solving is your forte.
Skills to master:
• Proactive threat identification and mitigation.
• Foundational knowledge in cybersecurity.
• Understanding of security protocols and standards.
• Proficiency in analyzing network traffic.
• Expertise in log examination.
• Skills in malware dissection and analysis.
• Effective communication abilities.

The analyst trajectory is frequently suggested as an entry point into the cybersecurity field. New analysts usually start with standard duties under the tutelage of seasoned experts in threat management, thereby gaining practical experience and chances for professional development. Regardless of whether you have an IT or a completely different background, this role could serve as an ideal starting point.
Developing a robust understanding of IT principles is crucial. One can achieve this through online courses or by participating in workshops focusing on networking, systems management, or basic cybersecurity—though it’s advised to grasp IT essentials first before diving into cybersecurity.

CompTIA Security+: An excellent entry-level certification providing the essential skills needed for a career in security analysis.
CompTIA Cybersecurity Analyst (CySA+): A more advanced credential tailored to the specialized skills of an analyst.

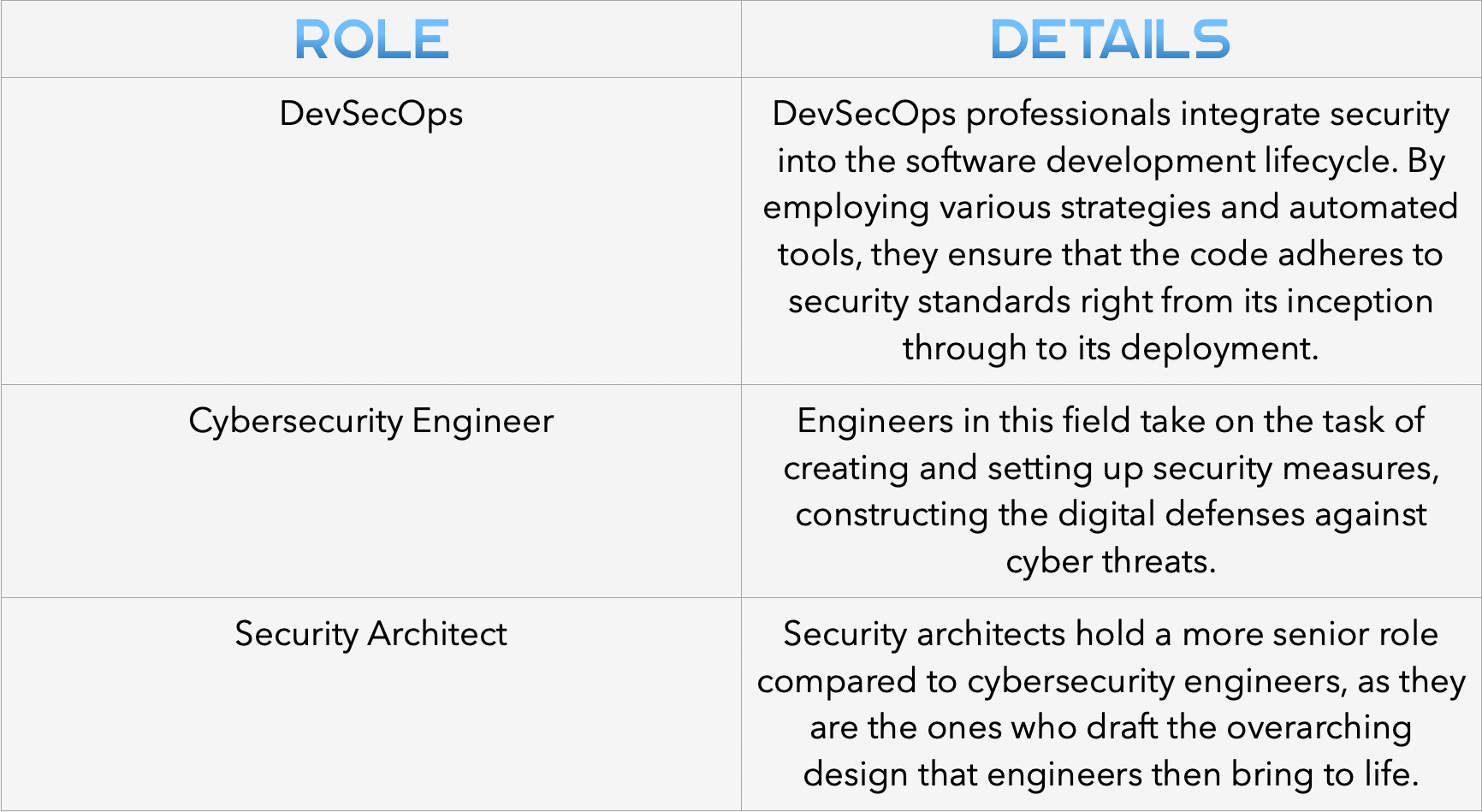
Cybersecurity engineers are the architects and mechanics of the security infrastructure. They conceptualize, develop, and deploy security solutions, while also overseeing the operations to confirm they support the organization’s overarching security strategy.
Choose this path if:
• You enjoy constructing and assembling components like building blocks.
• Technology excites you.
• Customizing and fine-tuning software to meet specific requirements appeals to you.
• You want to be the backbone of technical defense against cyber threats.
Skills to master:
• Basics of project management.
• Deep comprehension of cybersecurity concepts, principles, and frameworks.
• Effective teamwork and communication abilities.
• Expertise in both cloud and traditional on-site infrastructure.
• Proficiency with various operating systems and virtualization tools.
• Understanding of networking and security measures for networks.
• Competence in scripting and one or more programming languages.

This career track demands both experience and a high level of technical skill. While a significant number of cybersecurity engineers have degrees in computer science or related fields, formal education isn’t strictly necessary.
To embark on this path, it’s essential to have robust expertise in computing and IT systems, along with an in-depth grasp of cybersecurity principles, and the capability to integrate these areas effectively.

CompTIA Advanced Security Practitioner (CASP+) or Certified Systems Security Practitioner (SSCP): These qualifications are well-respected and cover critical engineering competencies.
AWS Certified Security – Specialty or Microsoft Certified: Azure Security Engineer Associate (AZ-500): Holding these certifications can enhance your appeal to employers looking for expertise in cloud security.

Specialists in Cybersecurity Governance, Risk, and Compliance (GRC) are tasked with upholding top security standards and ensuring compliance with global laws through strategic planning and conducting ongoing audits for risks and vulnerabilities.
Engaging in a career focused on cybersecurity governance and risk management means you’re in charge of shaping and looking after an organization’s complete security blueprint. This role encompasses devising cybersecurity policies, overseeing their application, and measuring their success.
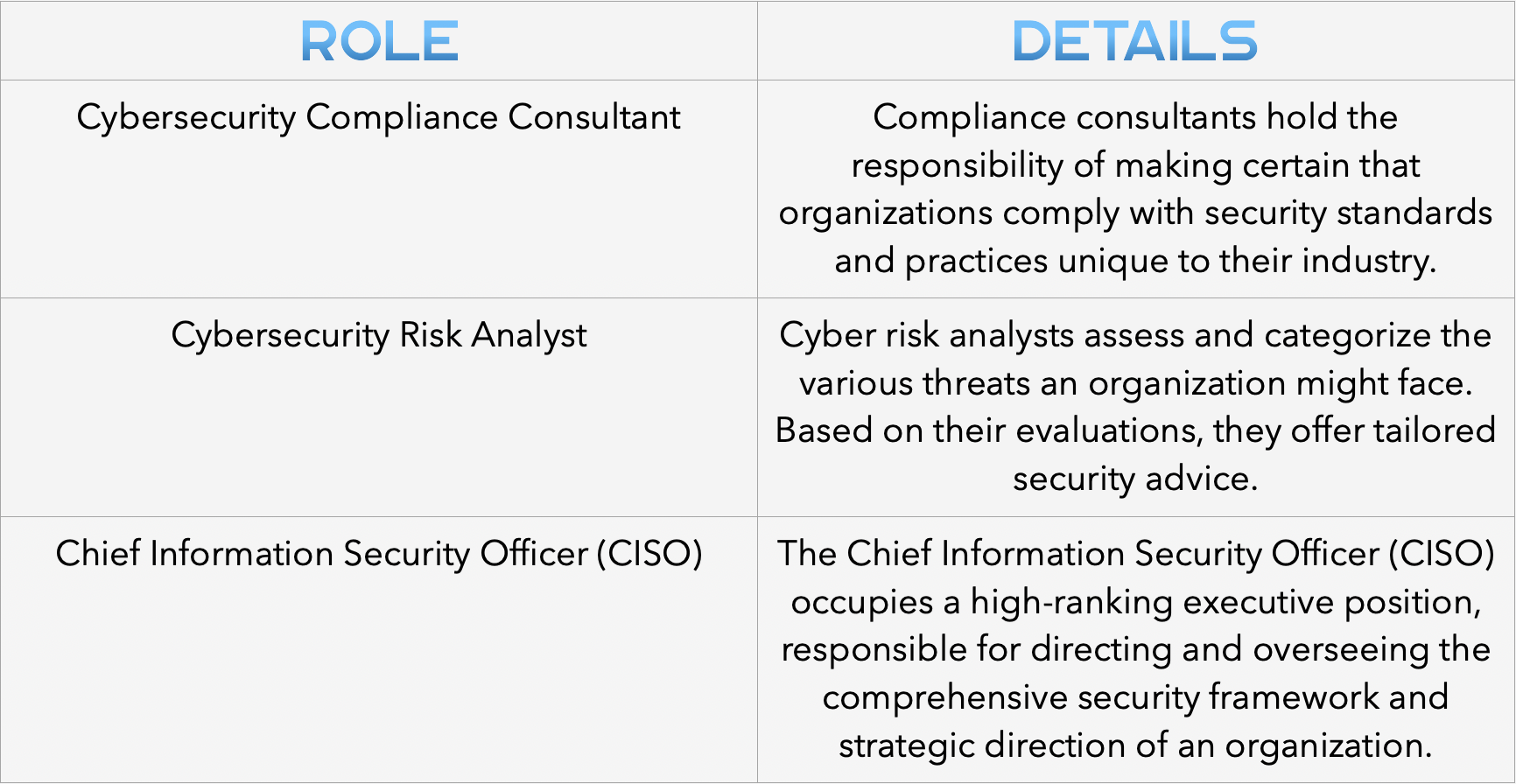
Choose this direction if:
• Leadership comes naturally to you.
• You possess a robust sense of accountability.
• Strategic planning excites you.
Skills you should develop:
• Exceptional communication abilities.
• Understanding of business organization and operational procedures.
• Familiarity with cybersecurity legal frameworks, standards, and regulations like GDPR, PCI DSS, and ISO 27001.
• Expertise in managing risks.
• Proficiency in managing projects.

Understanding the basics and frameworks of cybersecurity is essential for roles in governance and risk management. You need to integrate these principles into a coherent cybersecurity plan that adheres to sector-specific regulations.
Starting positions often include roles like a junior cybersecurity compliance consultant. It’s not unusual for individuals with backgrounds in various auditing fields, particularly IT auditing, to move into cybersecurity GRC roles.
Although a formal education isn’t strictly necessary for a career in governance and risk management, possessing a degree related to IT, coupled with recognized industry certifications, can significantly accelerate your professional growth.

Certified in Governance
Risk and Compliance (CGRC)
Certified Information Systems Auditor (CISA)
Certified in Risk and Information Systems Control (CRISC)
Certified in Risk and Information Systems Control (CISSP)

We’ve just taken a brief look at the diverse and dynamic career options within cybersecurity.
The cybersecurity sector is in dire need of enthusiastic individuals eager to impact positively. As explored, this field isn’t confined to just hacking—it’s a broad and profound domain brimming with opportunities for anyone looking to forge a career.
Regardless of whether your background is in computing or another discipline, there’s a niche in cybersecurity tailored to your abilities and passions.
Pursue what excites you, acquire knowledge, earn certifications that matter in the industry, and kickstart your journey with an entry-level position to amass valuable experience.
Accumentum® is the leading training provider for a vast array of technology vendors including AWS, Cisco, CIW, CompTIA, EC-Council, Fortinet, GIAC, HRCI, ISACA, ITIL, Microsoft, Palo Alto, PMI, Scrum, SHRM, Veritas, VMWare, and more.


